|
 This
worm will spread from vulnerable IIS server to vulnerable IIS server and,
on the 20th of July 2001, fire up packets from infected machines towards
the www.whitehouse.gov site, in what could result in a denial of service
attack. What's worse, the worm opens the door to new attacks. The worm
will then proceed to sleep for a few days and then resume its infection
phase. This
worm will spread from vulnerable IIS server to vulnerable IIS server and,
on the 20th of July 2001, fire up packets from infected machines towards
the www.whitehouse.gov site, in what could result in a denial of service
attack. What's worse, the worm opens the door to new attacks. The worm
will then proceed to sleep for a few days and then resume its infection
phase.
 The
worm's spread has been analyzed and graphed by caida The
worm's spread has been analyzed and graphed by caida
|
|
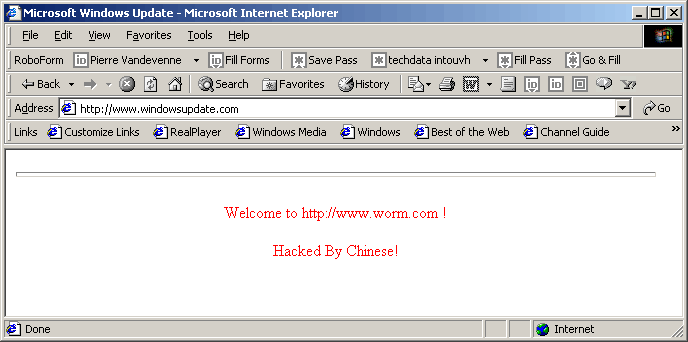
 At
the time this is being written, some of the Microsoft Windows Update sites
themselves have been reported to be infected. It is clear that if the
servers supposed to deliver the updates are themselves susceptible to
attacks, this raises fundamental questions on the security of the whole
infrastructure... At
the time this is being written, some of the Microsoft Windows Update sites
themselves have been reported to be infected. It is clear that if the
servers supposed to deliver the updates are themselves susceptible to
attacks, this raises fundamental questions on the security of the whole
infrastructure...
|